Showing results 1 - 20 of 1746 for "Englishtivi.com💥🏹🧿English tivi - Improve Your English Skills💥🏹🧿Englishtivi - Help You Change Your Life!"
BLOG POST - https://www.cisecurity.org/insights/blog/a-day-in-the-life-with-a-principal-software-engine...
A Day in the Life with a Principal Software Engineer
At CIS, we have a team of our experts working with a global community of cybersecurity professionals. Together, they help develop tools and resources ...
WHITE PAPER - https://www.cisecurity.org/insights/white-papers/cis-passive-network-sensor-placement
CIS Passive Network Sensor Placement
Your network sensor placement affects your ability to detect malicious traffic without affecting network performance. Here's how to improve your deplo...
BLOG POST - https://www.cisecurity.org/insights/blog/supporting-your-secure-cloud-goals-our-2023-year-i...
Supporting Your Secure Cloud Goals: Our 2023 Year in Review
2023 was a year full of efforts to help support you in meeting your secure cloud goals. Here's a look back at just a few of them....
BLOG POST - https://www.cisecurity.org/insights/blog/fast-track-your-implementation-of-essential-cyber-...
Fast-Track Your Implementation of Essential Cyber Hygiene
Our implementation guide works as a ladder to help you rapidly adopt IG1 of the CIS Controls and achieve essential cyber hygiene....
BLOG POST - https://www.cisecurity.org/insights/blog/balancing-your-healthcare-cybersecurity-and-compli...
Balancing Your Healthcare Cybersecurity & Compliance Efforts
Need a way to streamline your healthcare cybersecurity and compliance efforts? Here's how resources from CIS can help your organization....
BLOG POST - https://www.cisecurity.org/insights/blog/congratulations-youre-compliant-charting-your-path...
Congratulations, You're Compliant: Charting Your Path Ahead
What comes next after you've achieved compliance? We've got seven things for your consideration. A CIS SecureSuite Membership can help....
BLOG POST - https://www.cisecurity.org/insights/blog/6-mitigation-strategies-to-make-the-most-of-audit-...
6 Mitigation Strategies to Make the Most of Audit Results
Audits are valuable tools that help you to identify potential risks, inefficiencies, and gaps. Here's how to make the most of your audit results....
BLOG POST - https://www.cisecurity.org/insights/blog/how-security-controls-can-improve-your-cybersecuri...
How Security Controls Can Improve Your Cybersecurity Posture
By Sean Atkinson, Chief Information Security Officer, CIS® Security is a journey, not a destination. It is important to understand that as security an...
BLOG POST - https://www.cisecurity.org/insights/blog/build-a-robust-continuous-audit-program-in-10-step...
Build a Robust Continuous Audit Program in 10 Steps
Want visibility of control deficiencies, potential fraud, and compliance issues? A continuous audit program can help. Here's how you can get started....
MEDIA MENTION - https://www.cisecurity.org/about-us/media/media-mention/32-free-cybersecurity-training-reso...
32 Free Cybersecurity Training Resources for SMBs
32 free resources from sources like the Infosec Institute, SANS, CIS, and the FTC to help you develop and improve on your cybersecurity training progr...
BLOG POST - https://www.cisecurity.org/insights/blog/review-revise-repeat-snapshot-your-cybersecurity-r...
Review, Revise, Repeat: Driving a Cybersecurity Roadmap Home
The last step with your cybersecurity roadmap involves examining the plan you've implemented, revising and streamlining, and starting the process anew...
BLOG POST - https://www.cisecurity.org/insights/blog/how-to-calculate-your-organizations-ransomware-ris...
How to Calculate Your Organization's Ransomware Risk
Ransomware remains both a prevalent and impactful type of attack. Here's a tool to help you calculate your organization's ransomware risk....
SPOTLIGHT - https://www.cisecurity.org/insights/spotlight/election-security-spotlight-how-does-ei-isac-...
Election Security Spotlight – How Does EI-ISAC Help Members?
In this Election Security Spotlight, the Elections Infrastructure Information Sharing an Analysis Center (EI-ISAC) explains how it helps members....
NEWSLETTER - https://www.cisecurity.org/insights/newsletter/how-to-secure-your-home-network-against-cybe...
How to Secure Your Home Network Against Cyber Threats
Here is a list of steps you can take going forward to secure your home network and keep it safe against potential cyber threats....
BLOG POST - https://www.cisecurity.org/insights/blog/cis-controls-help-secure-home-network
How 4 of the CIS Controls Can Help Secure Your Home Network
Facing everything from viruses to malware, home and personal networks can be just as vulnerable to cyber crime as organizational systems. We spoke wit...
BLOG POST - https://www.cisecurity.org/insights/blog/pci-cis-partners-in-data-security
PCI & CIS: Partners in Data Security
CIS and PCI SSC work together on an ongoing basis to increase payment data security everywhere. Here's a look at how....
BLOG POST - https://www.cisecurity.org/insights/blog/secure-configurations-for-remote-endpoints-with-ci...
Secure Configurations for Remote Endpoints with CIS-CAT Pro
CIS-CAT Pro v4 gives you a way to manage the secure configurations of your systems – even when they're located in remote environments.[…]...
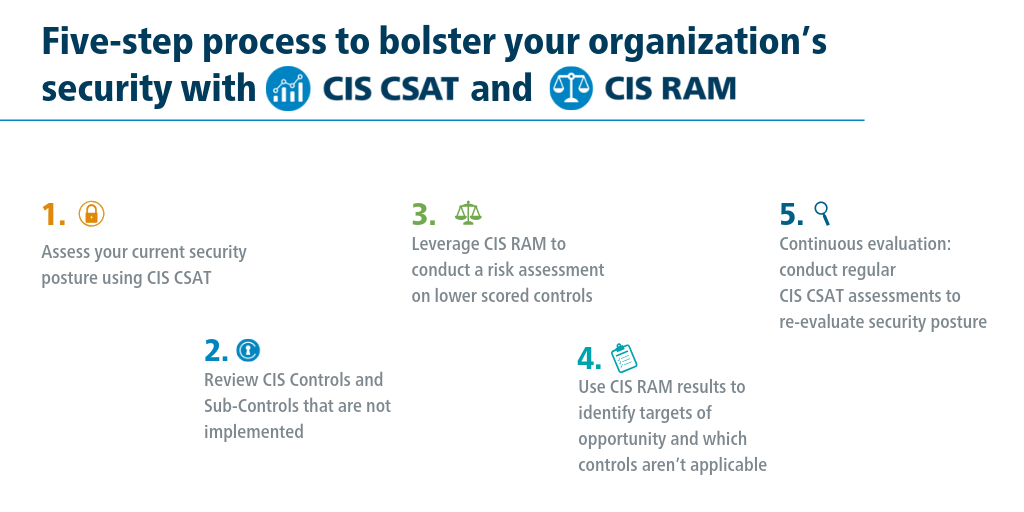
BLOG POST - https://www.cisecurity.org/insights/blog/assessing-risk-and-security-posture-with-cis-contr...
Assessing Risk and Security Posture with CIS Controls Tools
By Sean Atkinson, Chief Information Security Officer, and Phil Langlois, CIS Controls Technical Product Manager The CIS Controls are used by organizat...
BLOG POST - https://www.cisecurity.org/insights/blog/how-to-create-an-efficient-governance-control-prog...
How to Create an Efficient Governance Control Program
You need to account for several factors when building an efficient governance control program. Here's how CIS SecureSuite can help....
WEBINAR - https://www.cisecurity.org/insights/webinar/effective-implementation-of-the-cis-benchmarks-...
Effective Implementation of the CIS Benchmarks and CIS Controls
It’s not unusual to be challenged by limited time, resources, or even knowing where to start when developing your cybersecurity plan. CIS SecureSuite...